Platform
Evolve Security Automation, a one-stop platform for all your cybersecurity needs.
Enjoy continuous IT protection, supported by real people, and backed by expert insights. We seamlessly blend Penetration Testing and Data Breach Assistance. Our testing insights help us craft personalised solutions, so you're ready for any cyber challenge.





Feeling cyber-stressed?
Evolve provides a variety of solutions designed to meet the needs of both large enterprises and medium-sized businesses. We assist in providing instant testing, prompt testing, deliver in-depth network insights, and tackle your company's most pressing threats with a priority-focused approach
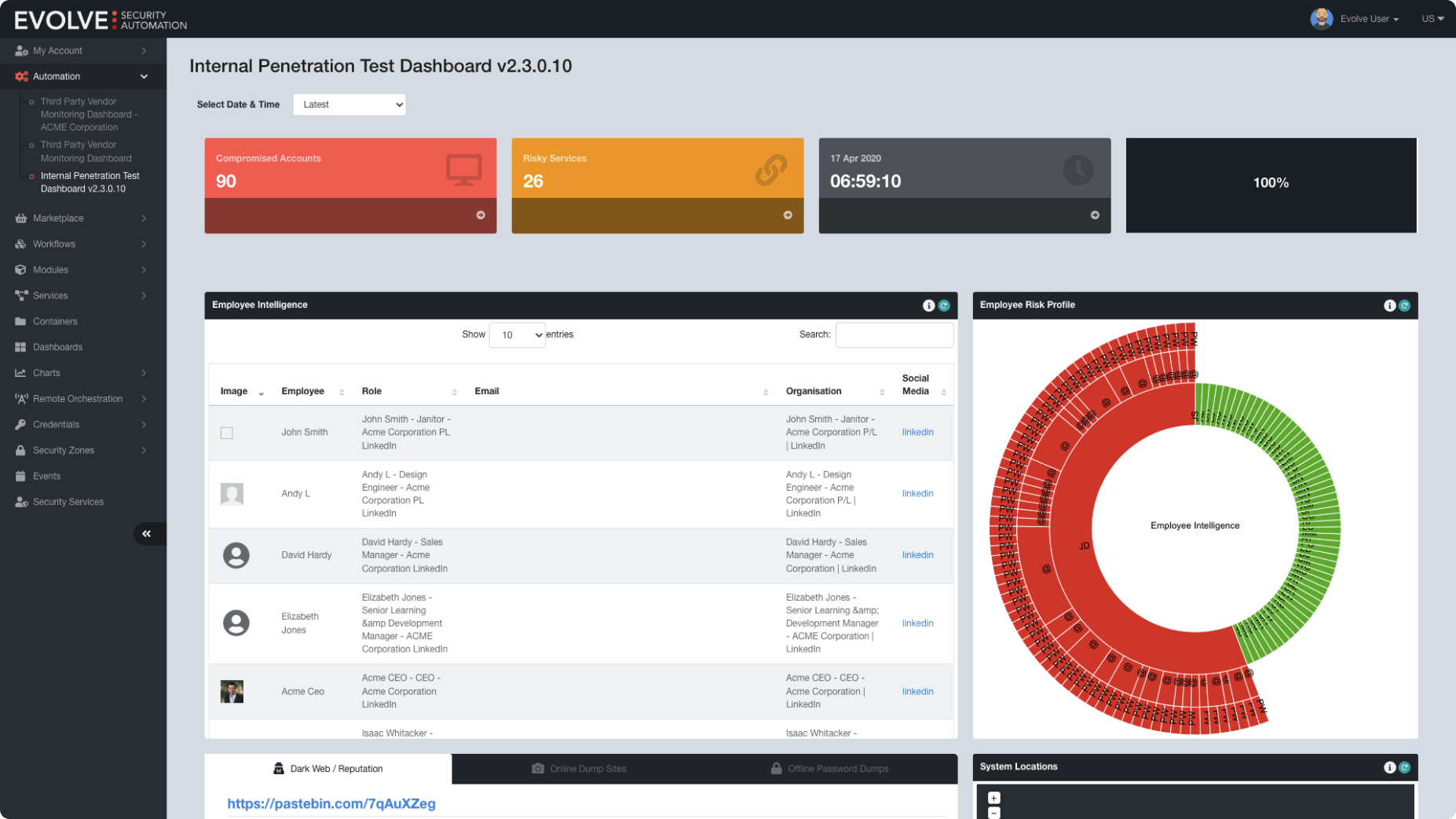
Cybersecurity Risk Management Simplified
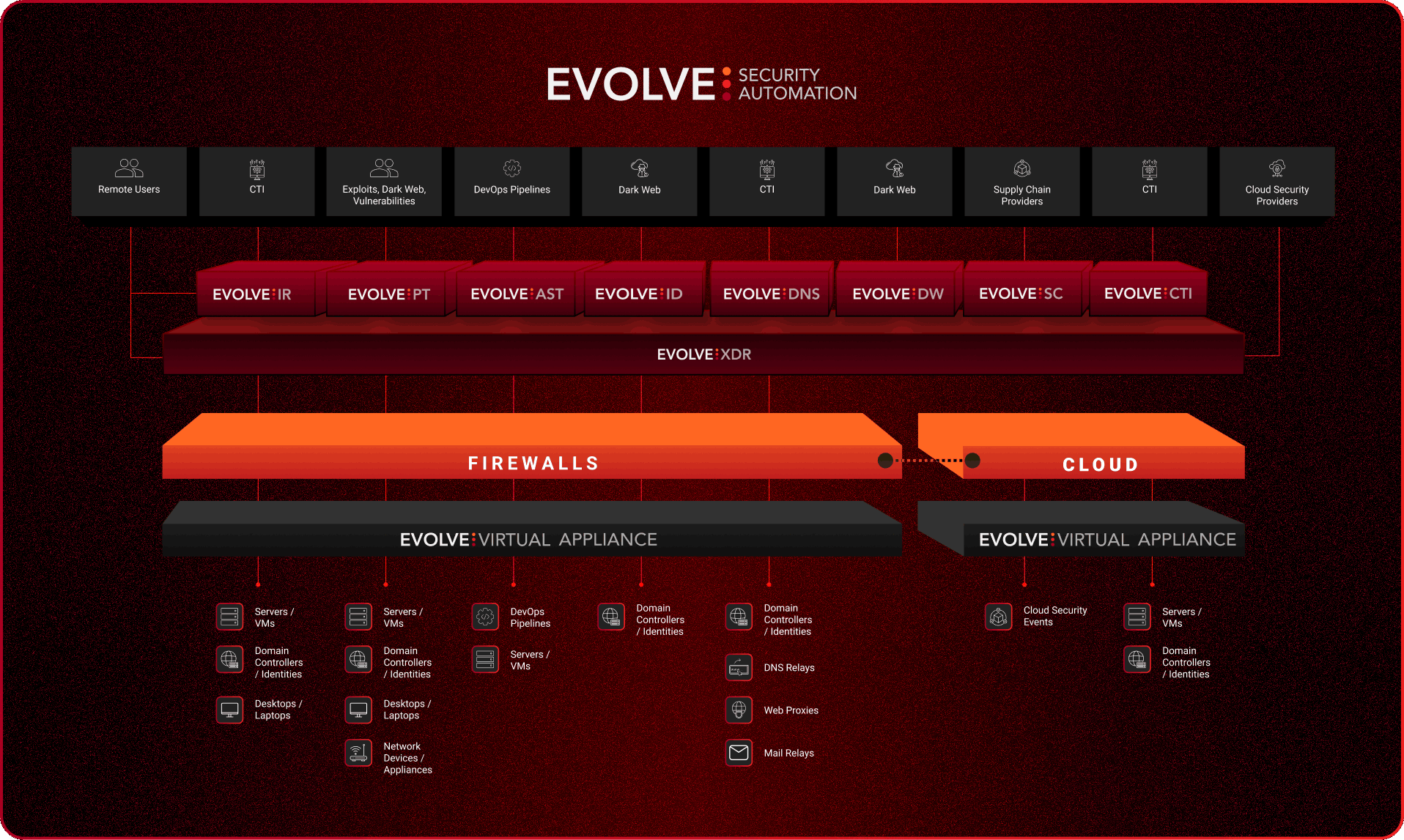
Evolve automates the most complex cybersecurity processes instantly, saving you time, reducing human intervention, and driving costs down. Evolve's built-in security capabilities automatically detect, prioritize, and remediate threats, so you can make faster business decisions with confidence. Choose your preferred Evolve tools and workflows to customize your solution and fit your unique cybersecurity needs.
Stay on top of the latest attack techniques relevant to your business and remediate critical risks with a complete cybersecurity platform.
Evolve provides your organisation with immediate skills and capability enhancements through specialist security workflows designed to streamline your operational security activities.
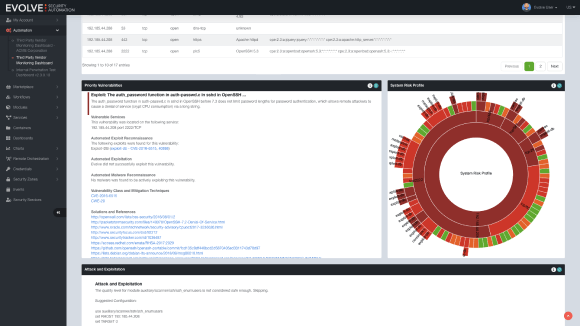
Continuous Security Validation
Evolve allows you to redistribute your security budgets within the context of your immediate business needs through flexible on-demand security capabilities that keep your business safe.
More protection, lower budget
Meet Compliance Requirements
Evolve maps all of the major security standards and frameworks to ensure you have the right security controls in place. From PCI-DSS to HIPAA, our automated workflows and dashboards help you monitor your compliance and harden your security posture.





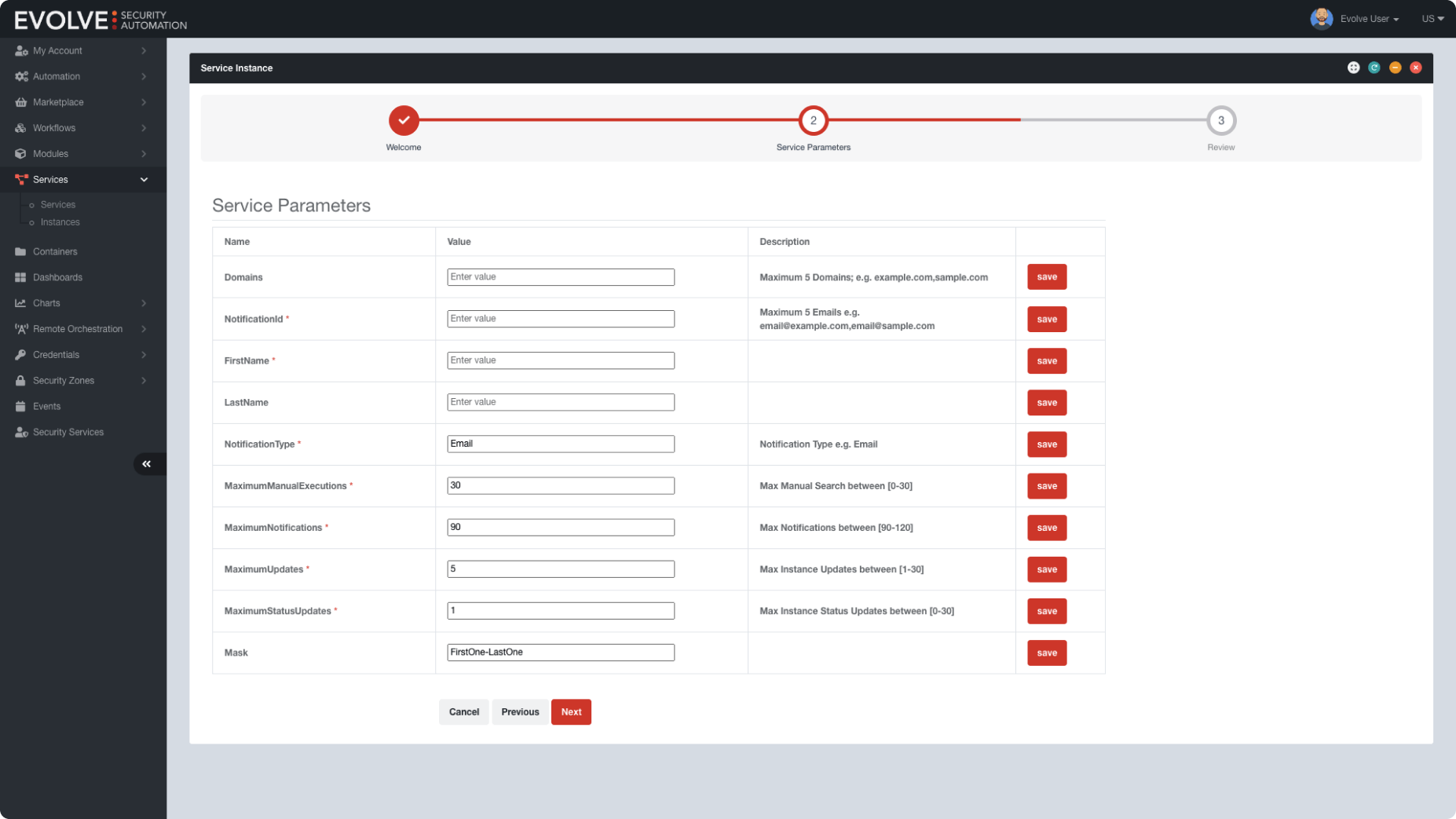
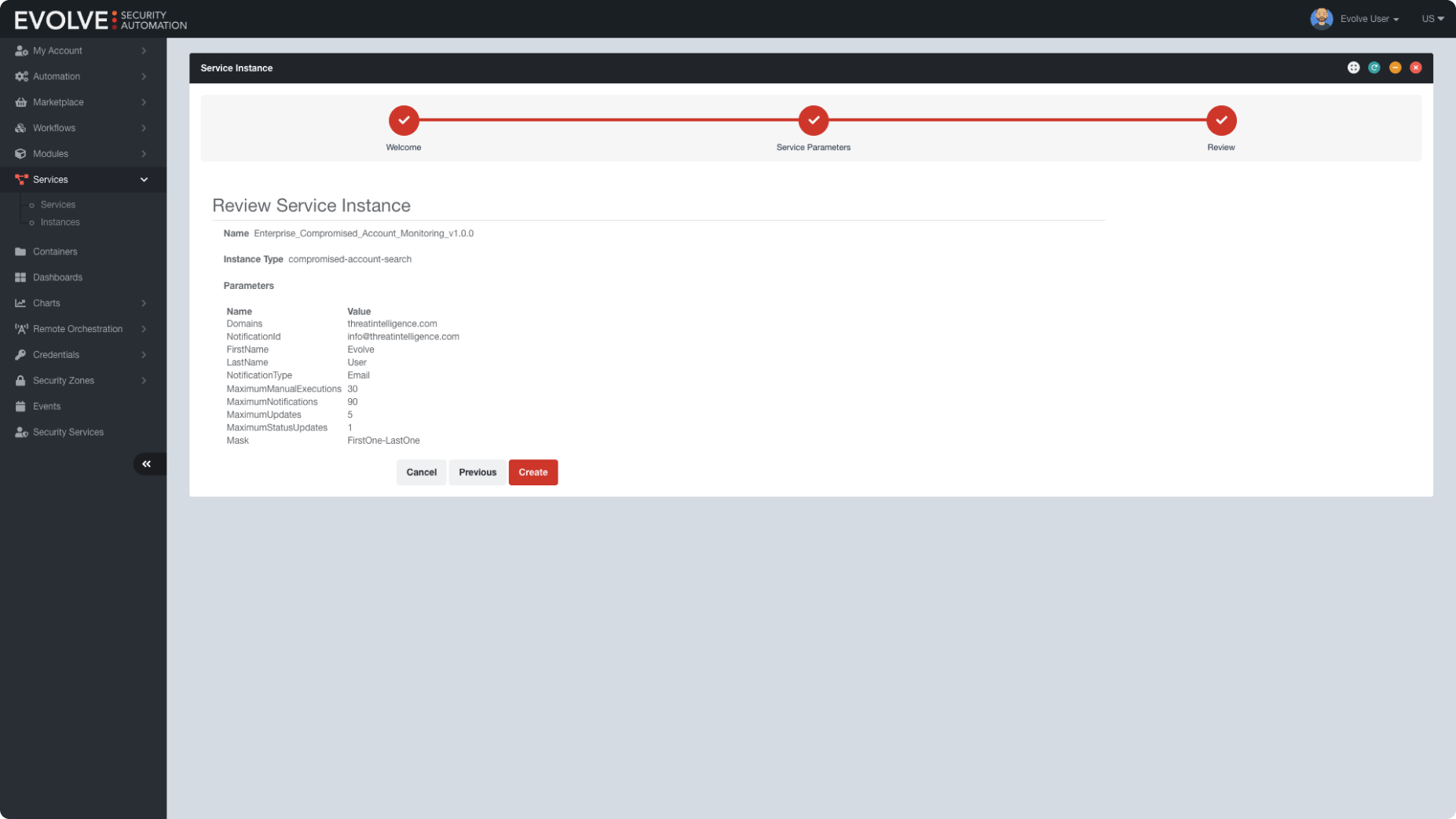
Get Up and Running in Minutes
Evolve tools are easy to use and integrate easily with your current security stack, providing a stress-free, seamless experience for your security team. Plus, they can be deployed in minutes so that you can take immediate action to remediate threats.
Evolve automatically generates pre-configured Evolve Virtual Appliances to be deployed into your corporate networks and on-premise data centers, supporting VMware or Hyper-V, and third-party cloud providers, including AWS and Azure.
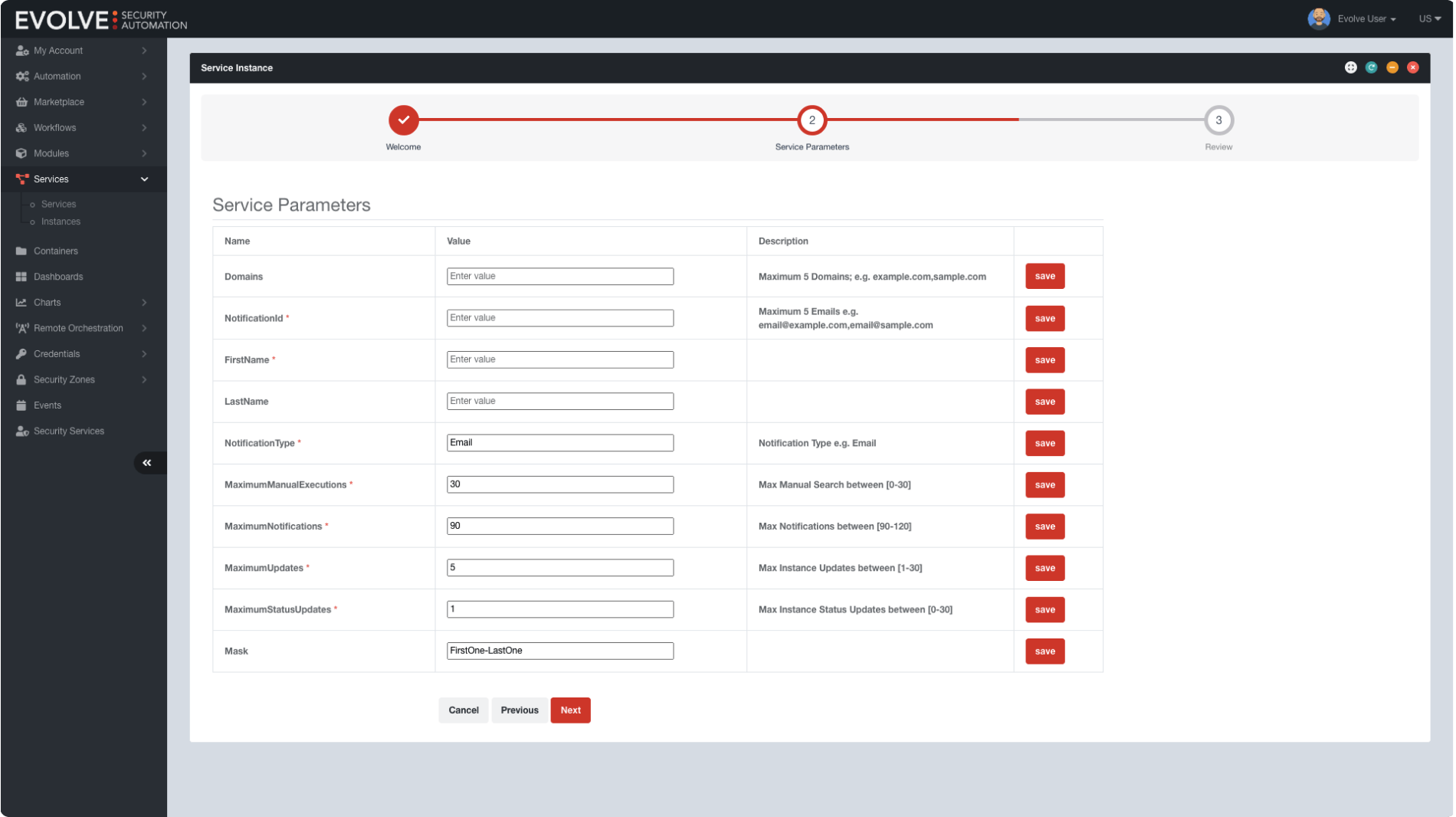
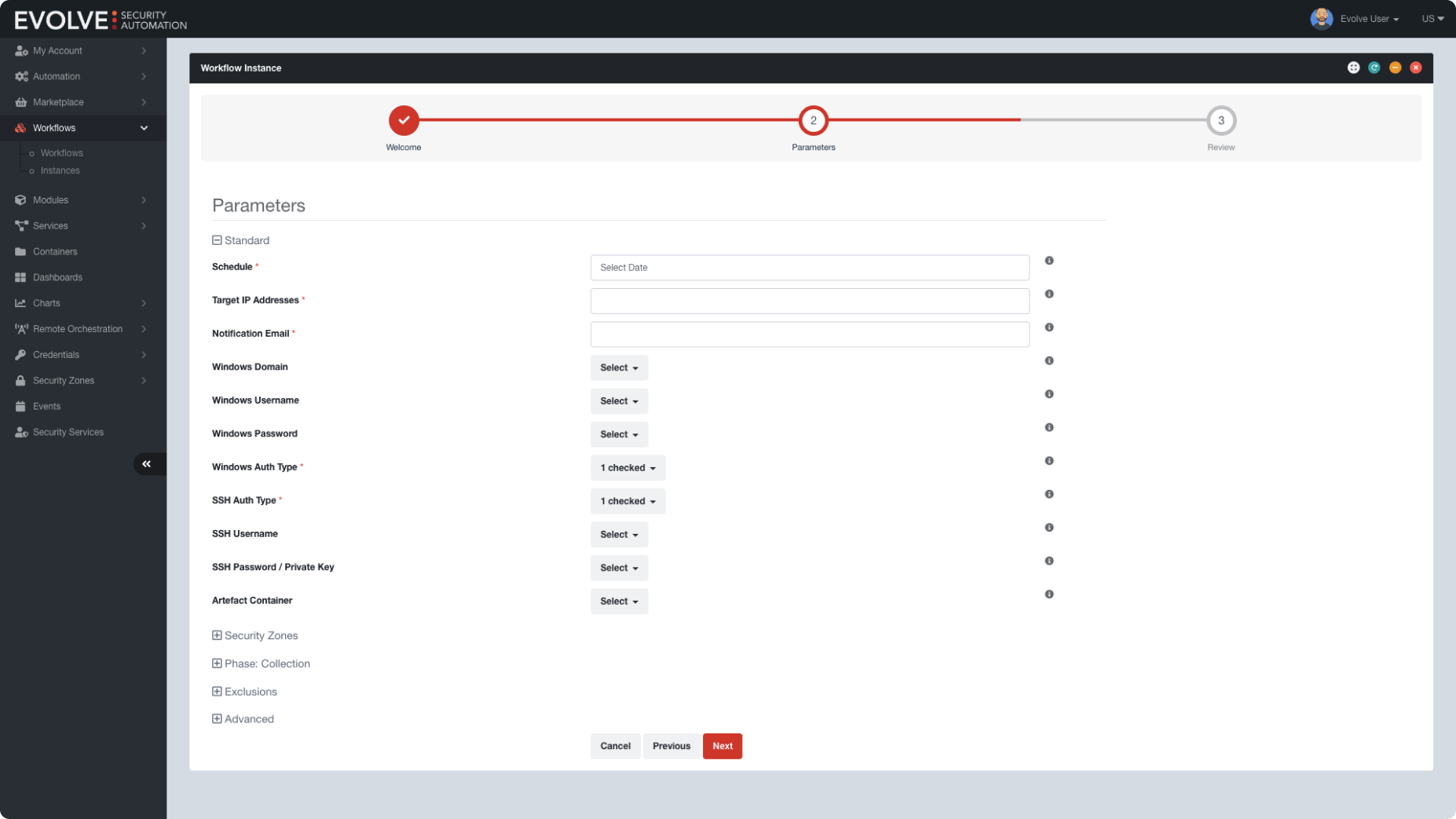
Explore all Evolve products
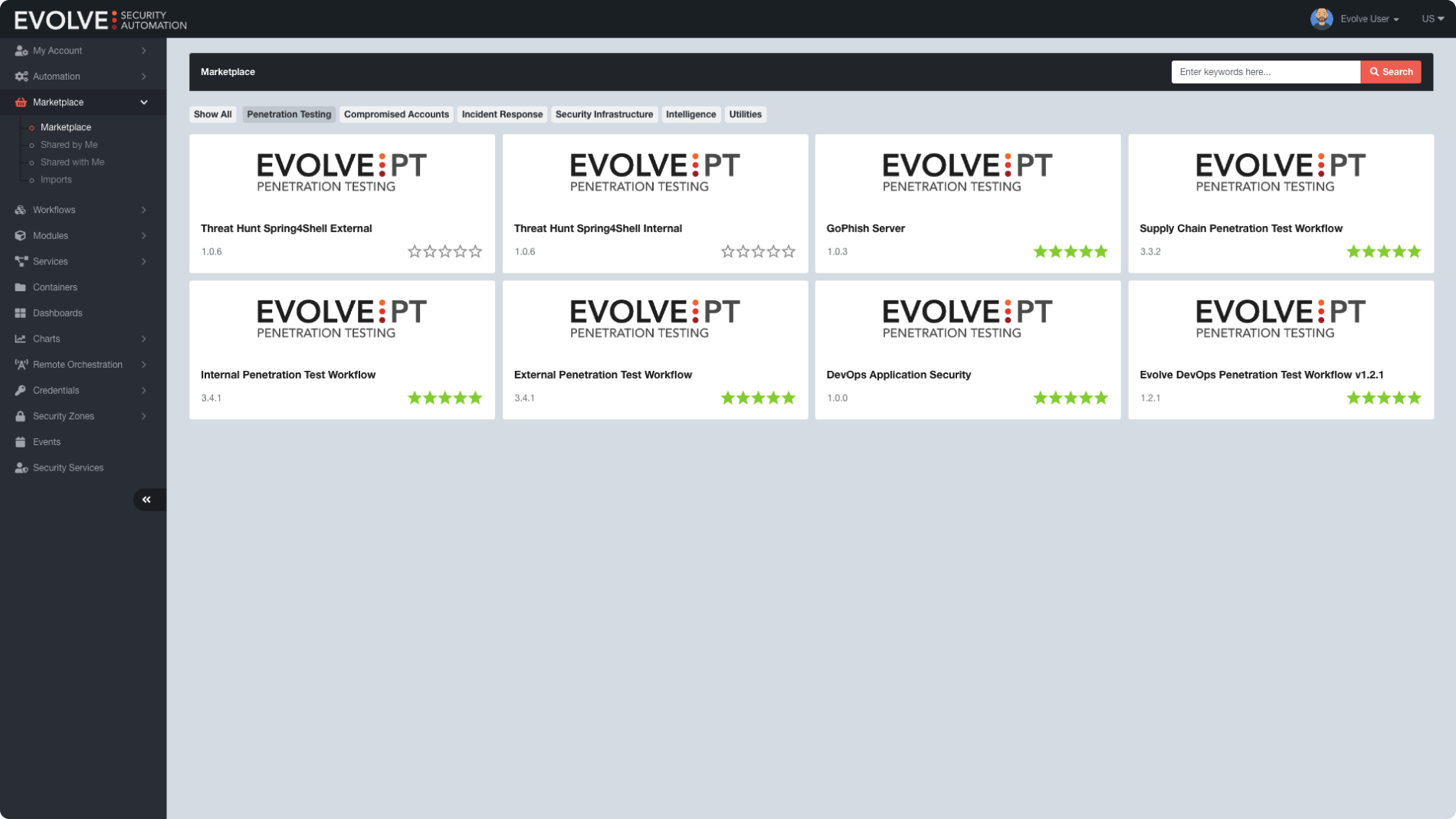
EvolvePT Continuous Penetration Testing
Get cost-effective continuous security validation by regularly testing your IT infrastructure.
EvolveXDR Extended Detection and Response
Get automated threat detection and response through data with extended detection and response.
EvolveIR Incident Response Tool
Automatically collect and analyze evidence, then naturally respond to security issues and contain breaches.
EvolveSC Supply Chain Monitoring
Detect critical Supply Chain Risks from your third-party vendors and avoid the #1 way that companies get breached.
EvolveAST Application Security Testing
Run regular automated application security tests to stay on top of the latest vulnerabilities and manage critical risks.

EvolveCTI Cyber Threat Intelligence
Automatically integrate Cyber Threat Intelligence into your security infrastructure for proactive protection.
EvolveID Leaked Password Monitoring
Protect your corporate accounts from breached passwords by automatically monitoring your email addresses and domain names.
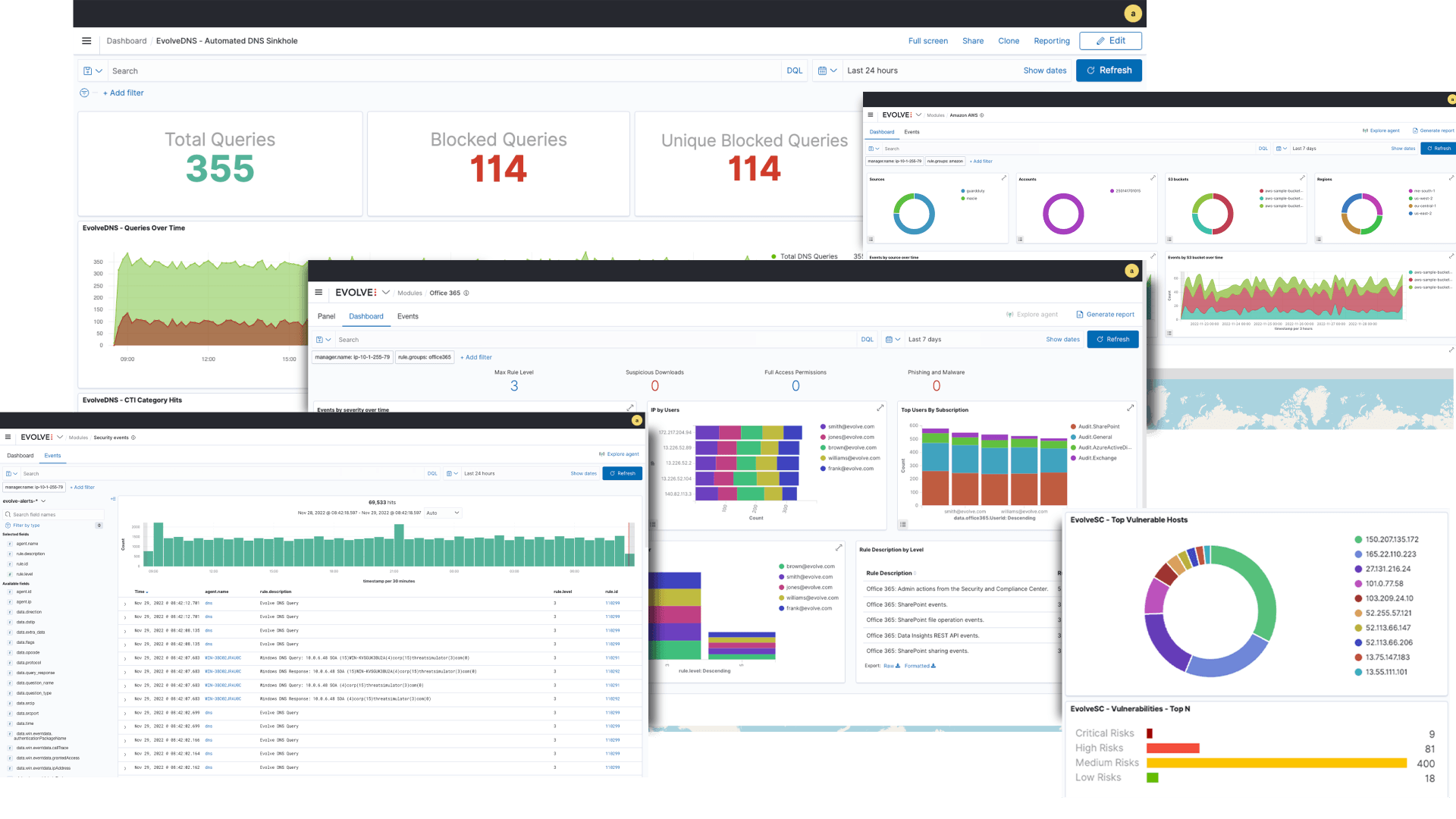
EvolveDNS Malicious Domain Detection
Automatically detects malicious domains and redirects the malicious DNS request.
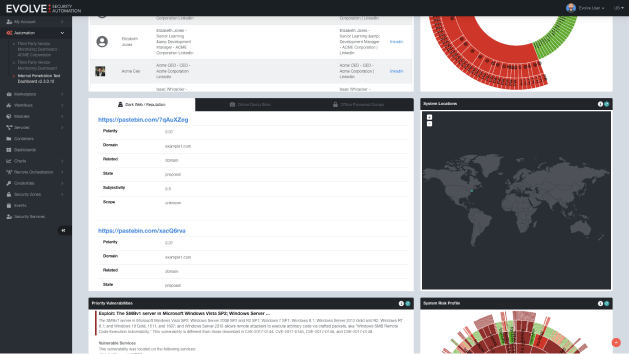
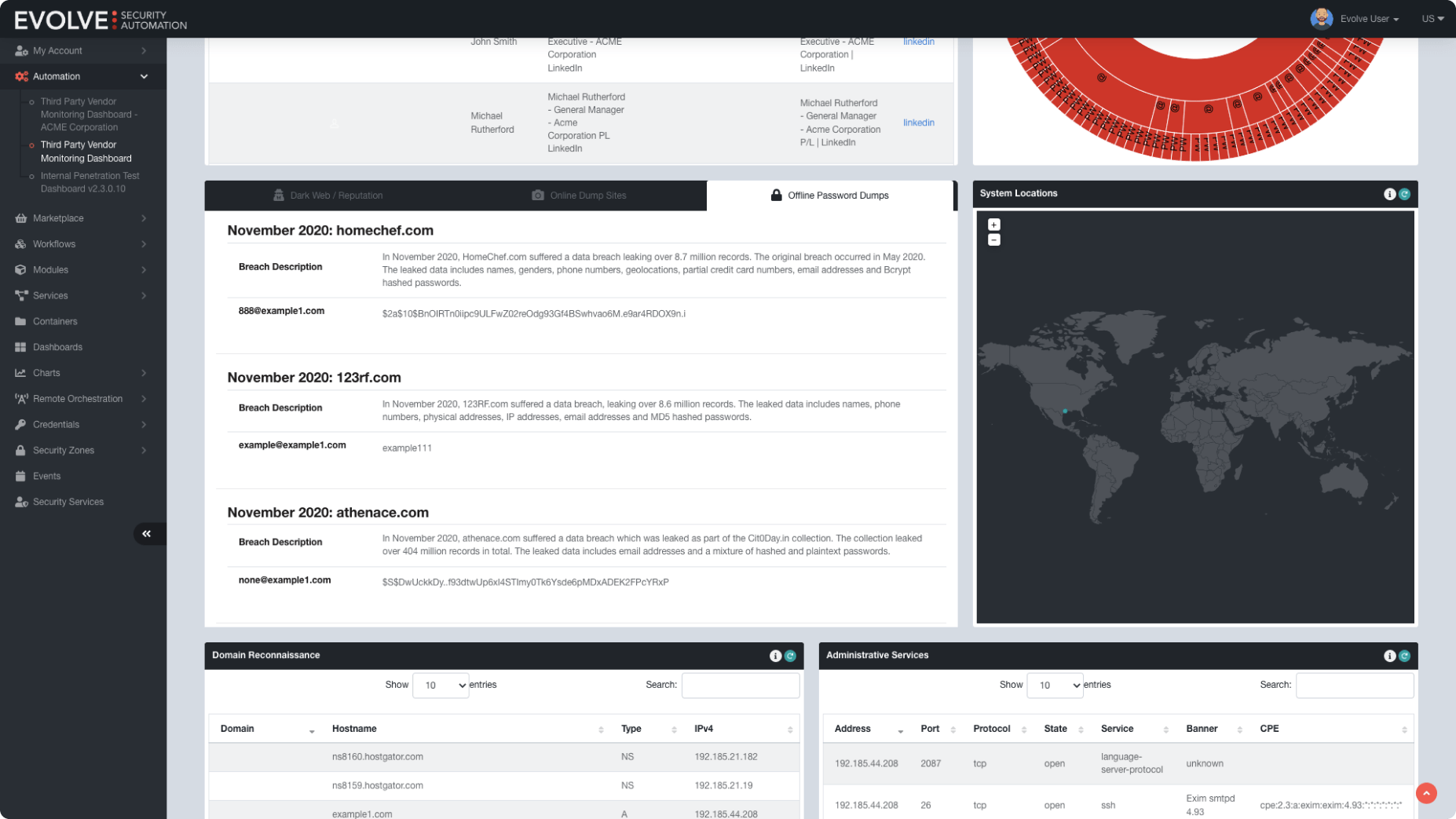
EvolveDW Dark Web Monitoring
EvolveDW monitors your domains and keywords on the dark web, alerting and preparing your team for action when data leaks or threats are detected.
Integrate security into your IT infrastructure and cloud providers
Choose from a wide range of on-demand integrations and
API integration capabilities to build your custom workflows.
Selected to conduct and manage penetration testing examinations for the Australian Government, our team members not only hold positions on the Board of Directors of CREST Australia and New Zealand, but also lead the CREST Technical Team.

With extensive experience in the longest running training course at Black Hat USA and a position on the Black Hat Asia Review Board, our trainers are renowned for their expertise in the most recent threats and the cutting-edge techniques to combat them.

Threat Intelligence contributes to the development of global security methodologies, standards, and libraries that are incorporated into industry-specific security regulations of the Open Web Application Security Project (OWASP).

The Team Behind Evolve
"Thanks to the exceptional Incident Response Management at Threat Intelligence, we were able to quickly address a major security breach of our network and mitigate the impact.
The team was able to identify the root cause of the breach, check for stolen privileged accounts, and company data that might have been exposed. They were also able to centralize and coordinate all of the necessary cyber security telemetry and response data that was relevant to the breach. The team's efforts were critical in helping us to quickly resolve this issue and protect our network.
We highly recommend TI's Incident Response team to any organization seeking top-notch cybersecurity expertise, quick and effective incident response, and a reliable partner in cybersecurity."
CISO
Healthcare
Enterprise
Ready to Get Started?
Is your organization looking for a complete cyber security solution? With our products and services, your team can take a propositive security posture. Let’s chat.