Enterprise Endpoint Security: Rapid Visibility, Unlimited Agents, and MITRE ATT&CK-Mapped Threats.

Maximize endpoint security with EvolveXDR
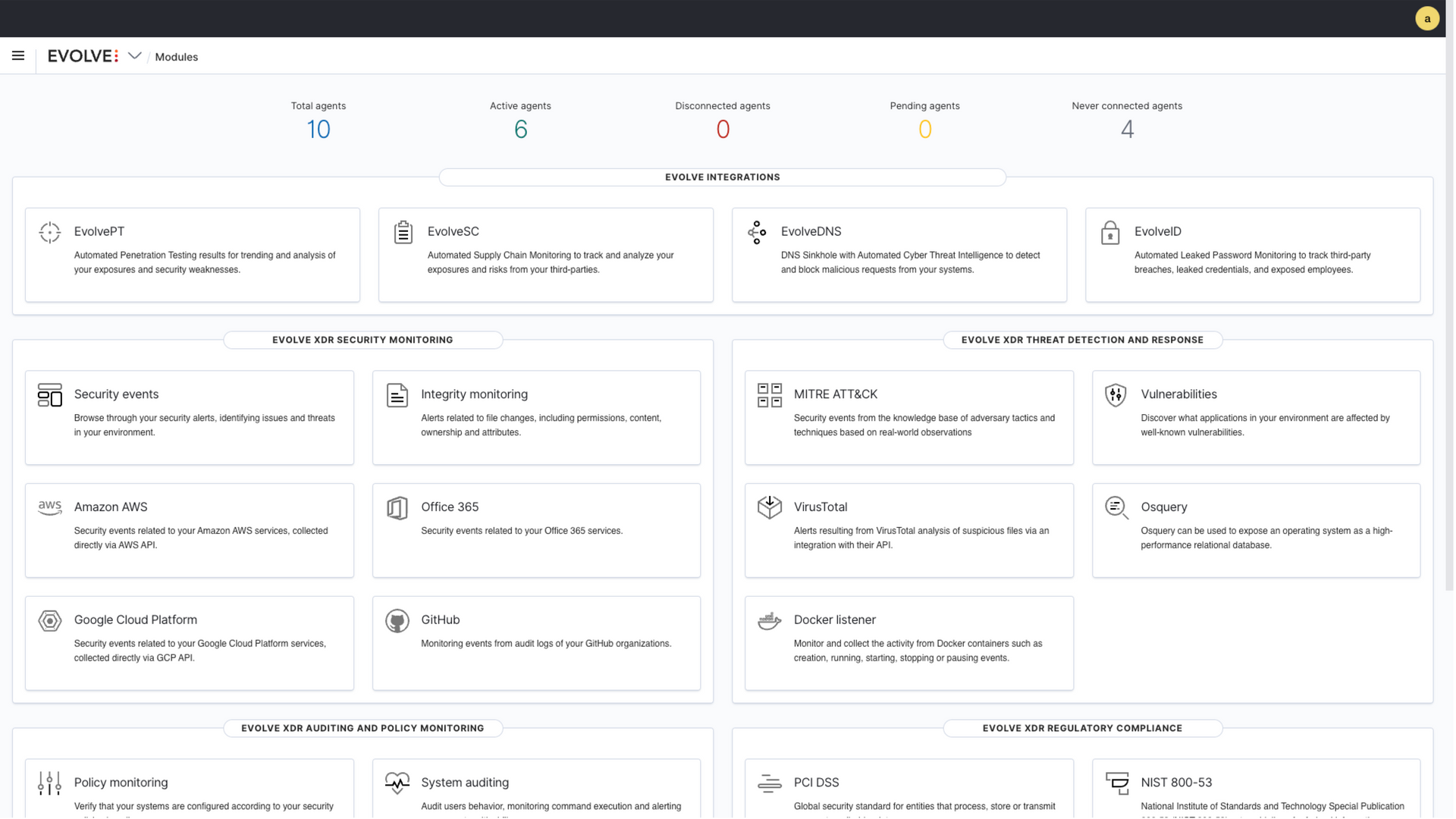
EvolveXDR goes beyond traditional endpoint security and gives you a truly holistic, data-driven view of your endpoints and the threats they face. With on-demand SIEM and unlimited EDR agents, you get rapid visibility into suspicious activities across all your endpoints, mapped to the MITRE ATT&CK framework. Keep your endpoints secure and free from security breaches with minimal effort.
Visibility Beyond the Endpoint
EvolveXDR gives you an unprecedented level of real-time visibility beyond the endpoint. You can observe your endpoints in real-time, no matter where they are located or how many endpoints you have. This makes it easy to detect security issues and compliance violations, and take swift action to address them. Evolve comes pre-installed with standards for compliance, including PCI DSS, SOC, ISO, FedRamp, and HIPAA and automatically visualizes gaps in your compliance requirements. It also has automated configuration assessments (CIS) to catalog your assets, making sure that your security settings remain up to date for optimal protection.
Scale with the Power of Data
Increased amounts of data don't always have to equate to increased complexity and resources. EvolveXDR leverages data retention and scalability to quickly ingest, correlate, and analyze vast amounts of data without sacrificing performance. It automatically orchestrates the service based on your data retention requirements and budget, helping you easily scale and grow with your data without additional complexity or expenses.
Trusted by





No Additional Resources
With EvolveXDR, you get the power of security software consolidation that minimizes manual effort. Avoid the time and additional expertise needed to make a SIEM solution effective — leave the heavy lifting to EvolveXDR from the start. Our security experts will take care of the hard work, so you can make the most of your subscription right away and start seeing a return on your investment immediately.
Utilize EDR agents to:
- Track systems and software versions
- Detect vulnerabilities
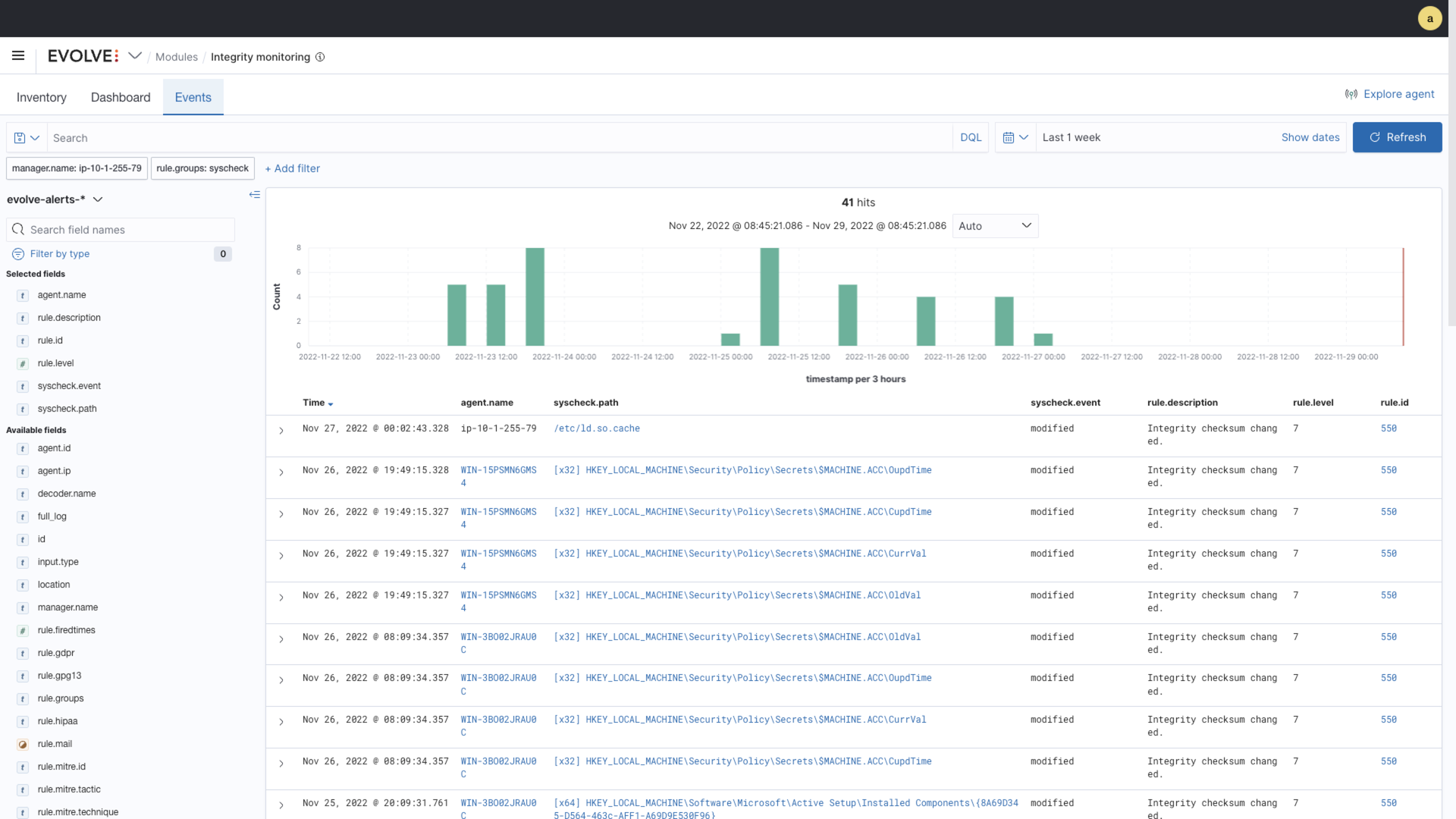
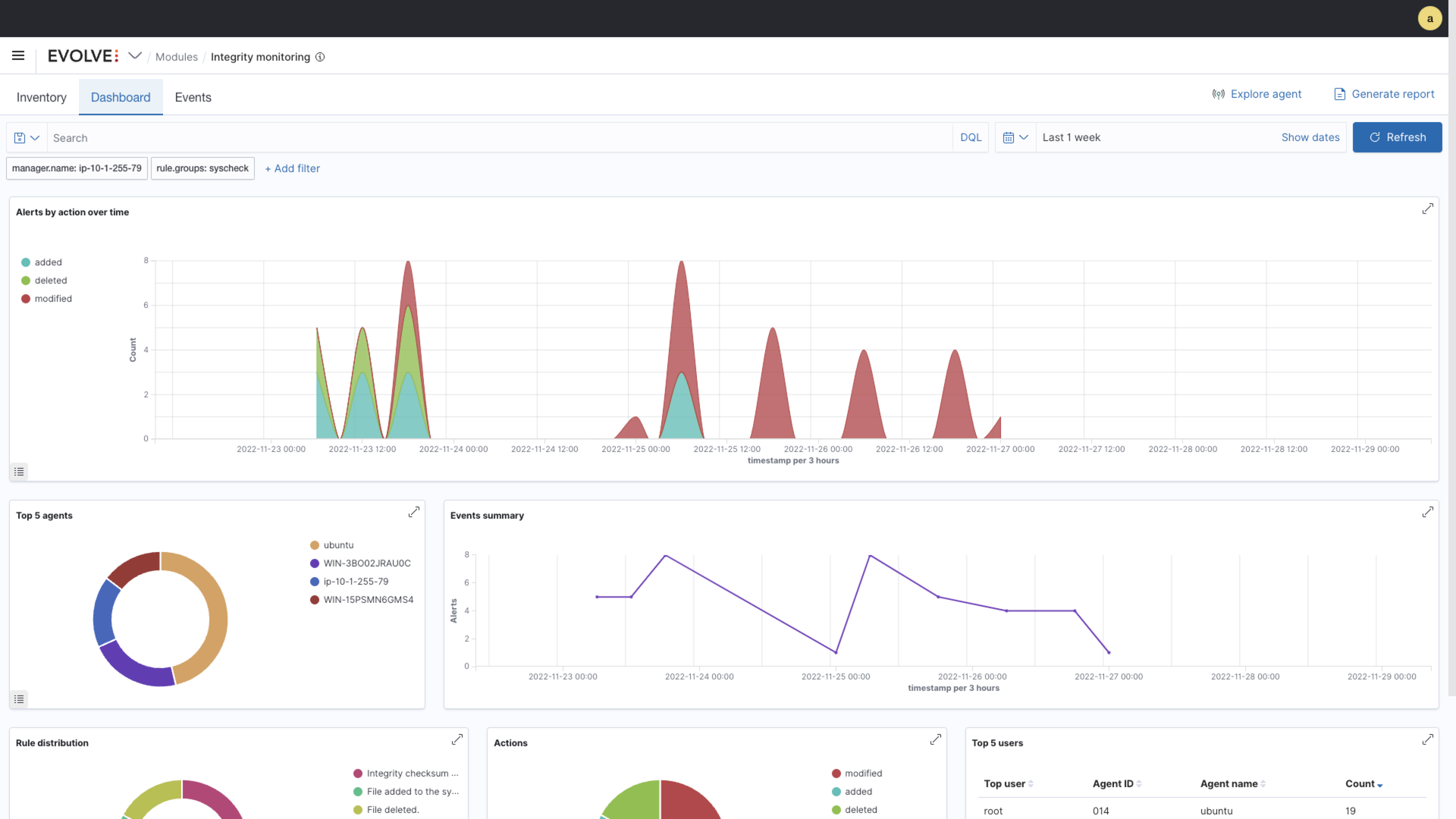
- Monitor file and registry integrity
- Monitor compliance events
- Enforce security and configuration policies

Unlimited EDR Agents
Monitor and collect data from as many endpoints as you want at no extra cost.

Immediate Security Monitoring
Get started in minutes and enable automatic detection of security breaches right away.

Automated Detection and Response
Detect threats faster with greater accuracy and get automated response capabilities out of the box.
Key Features of EvolveXDR:
- Unlimited EDR Agents
- Simple EDR Deployment
- Security Event Analysis
- Scalable Data Retention
- Mitre Att&Ck Mapping
- Breach Detection
- Automated Response
- Compliance Event Mapping
- Kql / Sql Query Support Timeframes
- And much more!
Selected to conduct and manage penetration testing examinations for the Australian Government, our team members not only hold positions on the Board of Directors of CREST Australia and New Zealand, but also lead the CREST Technical Team.

With extensive experience in the longest running training course at Black Hat USA and a position on the Black Hat Asia Review Board, our trainers are renowned for their expertise in the most recent threats and the cutting-edge techniques to combat them.

Threat Intelligence contributes to the development of global security methodologies, standards, and libraries that are incorporated into industry-specific security regulations of the Open Web Application Security Project (OWASP).

The Team Behind Evolve
FAQs
Got a question? We’re here to help.
-
What is XDR, and how is it different from traditional endpoint protection platforms (EPP) or security information and event management (SIEM) solutions?
XDR (Extended Detection and Response) is a security solution that unifies multiple security technologies and data sources into a centralized platform for threat detection and response. XDR differs from traditional EPP and SIEM solutions in that it integrates and correlates data from multiple sources, including endpoints, network, and cloud, to provide more comprehensive threat visibility and faster incident response.
-
What types of resources (e.g. hardware, software, personnel) are required to implement and maintain EvolveXDR?
EvolveXDR is a cloud-based solution, so organizations do not need to invest in additional hardware or software. However, organizations will need to allocate personnel resources to configure and manage the solution, as well as ensure proper integration with their existing security infrastructure.
-
What is the process for upgrading or scaling EvolveXDR solution as an organization's security needs evolve?
The process for upgrading or scaling the EvolveXDR solution depends on the specific needs of the organization. EvolveXDR is a cloud-based solution, so upgrades and scaling can typically be done with minimal disruption to operations.
-
What are some common use cases for XDR, and how can it help organizations better protect against advanced threats?
Common use cases for XDR include threat detection and response, incident investigation, and threat hunting. XDR can help organizations better protect against advanced threats by providing real-time threat visibility, automating incident response, and enabling security teams to quickly investigate and respond to security incidents.
-
What types of organizations benefit most from implementing an XDR solution, and what factors should be considered when selecting an XDR vendor?
Organizations of all sizes and industries can benefit from implementing an XDR solution, particularly those with complex IT environments or high-risk security profiles. When selecting an XDR vendor, organizations should consider factors such as the vendor's experience and expertise, product features, scalability, and compatibility with their existing security infrastructure.
-
What types of data sources does EvolveXDR integrate with, and how does it leverage that data to identify threats?
EvolveXDR can integrate with a wide range of data sources.
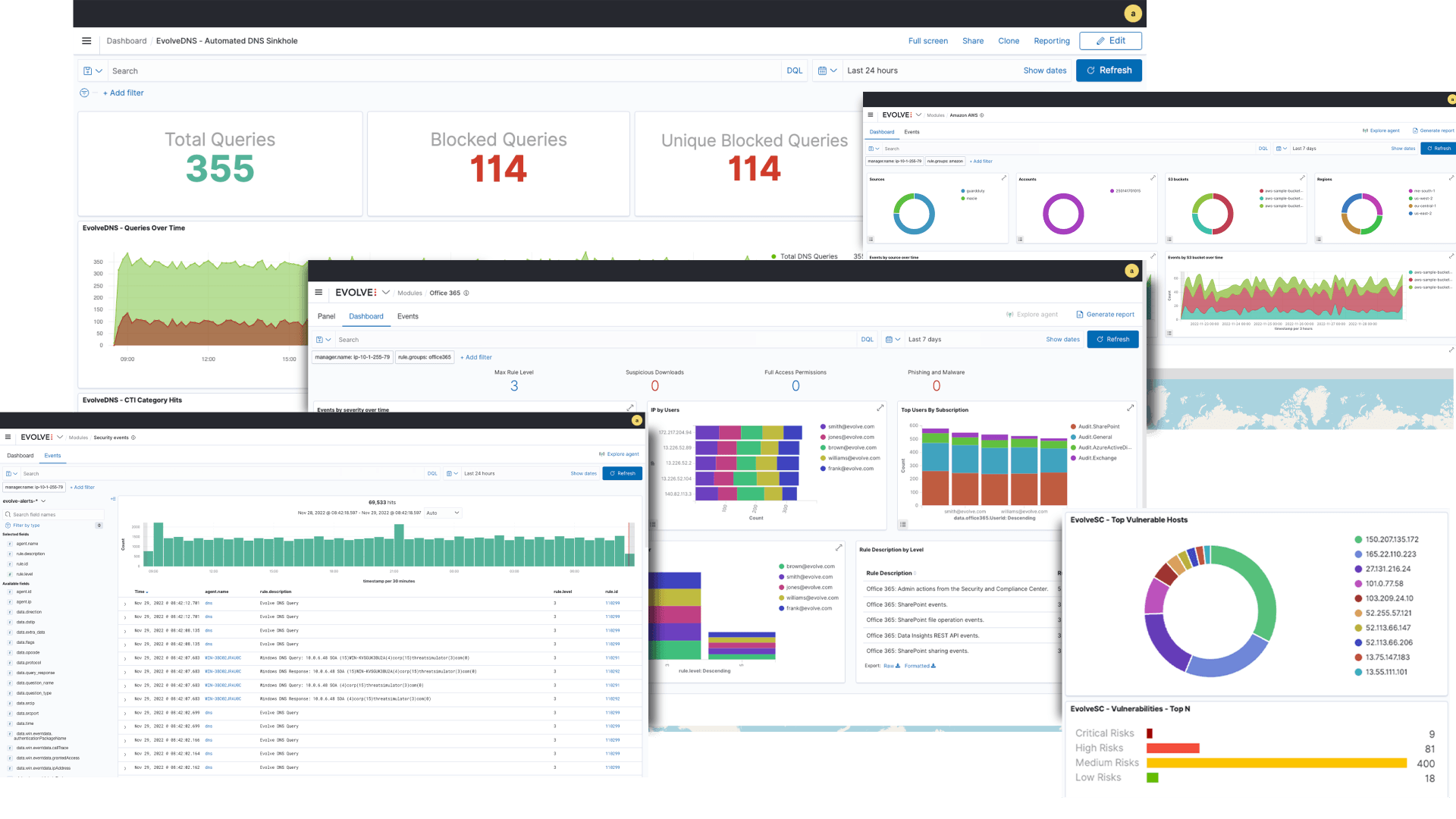
With EvolveXDR's integration with Mimecast, OKTA, Office 365, and EvolvePT, you can ingest and centralize data from multiple sources into the EvolveXDR SIEM, giving you a complete and accurate picture of your security environment. By analyzing data from multiple sources, EvolveXDR can help you identify complex threats that may have otherwise gone unnoticed.
For example, by correlating logs from your Mimecast tenancy and your OKTA tenancy, you can identify potential phishing attacks targeting your employees that may have originated from a compromised email account. Similarly, by ingesting logs from your Office 365 tenancy, you can detect unauthorized access to sensitive data or suspicious behavior that may indicate a potential data breach.
Furthermore, by integrating with EvolvePT, EvolveXDR can incorporate data from your penetration testing activities, providing you with insights into vulnerabilities and attack patterns that may be present in your environment. And all these integrations are fully automated.
By analyzing this data alongside other security logs, you can identify gaps in your security posture and take proactive steps to address them.
-
What types of reporting and analytics capabilities does EvolveXDR offer?
EvolveXDR offers robust reporting and analytics capabilities to help you gain insights into your environment and detect potential threats. The hindsight report provides a succinct email digest of activity within the configured reporting period, enabling both operational and management teams to quickly gain insights into activity across the environment. In addition, EvolveXDR Dashboards provide pre-defined visualizations for services such as Automated Penetration Testing, Compromised Account Monitoring, DNS Sinkhole, vulnerability data, and compliance data. With these reporting and analytics capabilities, you can stay on top of potential threats and take proactive steps to secure your environment.
-
What is the process for deploying and configuring EvolveXDR, and how long does it typically take?
The process for deploying and configuring EvolveXDR will vary depending on factors such as the size of the organization and the complexity of the deployment. However, the cloud-based deployment option can be deployed in as little as 60 minutes, making it one of the fastest and easiest security solutions to deploy.
Simply import this service and launch an instance, selecting your desired EvolveXDR tier based on the estimated GB per day, data retention requirements and budget. Evolve will automatically orchestrate your EvolveXDR service (login as "admin" over HTTPS) to manage your EvolveXDR agents. EvolveXDR agents register on port 1515/TCP and send data on port 1514/TCP and 1514/UDP.
-
How does EvolveXDR support incident response, and what capabilities does it offer for investigating and containing security incidents?
EvolveXDR includes a range of incident response capabilities, including real-time alerts, automated incident response workflows, and customizable playbooks. Additionally, the solution provides detailed forensic analysis and investigation tools to help organizations quickly identify the root cause of an incident and contain it.
-
Can EvolveXDR be deployed in both on-premises and cloud environments?
Yes
-
How does EvolveXDR integrate with other security solutions, such as endpoint detection and response (EDR) or network detection and response (NDR) solutions?
The Evolve XDR easily integrates into third party data sources and technologies through an extensive range of pre-built out of the box APIs.
-
What types of ongoing maintenance and support are required for EvolveXDR, and what is the typical cost associated with these activities?
The Evolve XDR is extremely cost effective. Once the free of charge unlimited agents are deployed across the organisation the endpoints agents are then tuned to only collect relevant cyber security logs and third party sources to ensure You don't have to pay for unwanted or irrelevant data ingestion.
-
How does EvolveXDR handle false positives, and what steps can be taken to reduce the number of false positives generated?
The Evolve XDR maps all events against the MITRE attack framework. Additionally Threat Intelligence can also provide our extremely experienced SOC analysts to manage the Evolve XDR and perform level 1, Level 2 and Level 3 Triage to assist in the removal of false positives and significantly reduce the workload on Cyber and IT teams chasing false positives.
-
How can an enterprise measure the effectiveness of EvolveXDR?
The effectiveness of the Evolve MDR can be seen every month when the XDR monthly activity report is generated and the Cyber and IT teams can review the findings. The true test of an XDR is proven in its ability to identify, alert and stop potential breaches.
-
How does EvolveXDR differ from other XDR solutions on the market?
EvolveXDR stands out from other XDR solutions on the market by offering a comprehensive suite of security monitoring capabilities across a wide range of systems. This means that organizations can enjoy immediate visibility into security breaches and suspicious activity, which is mapped to the MITRE ATT&CK framework. By leveraging an on-demand SIEM and unlimited XDR agents, organizations can ensure that they have the necessary tools to detect and respond to threats quickly and effectively. Furthermore, EvolveXDR's advanced features such as Intrusion Detection, File Integrity Monitoring, Cloud Monitoring, Vulnerability Detection, System Security Policy Monitoring, and Compliance Monitoring provide organizations with a complete security solution that helps them to better protect their assets and data.
Ready to Get Started?
Is your organization looking for a complete cyber security solution? With our products and services, your team can take a propositive security posture. Let’s chat.