Stay Ahead of Cyber Threats: Detect Stealer Malware with Our Upgraded Solution
EvolveID provides on-going monitoring of your online accounts, ensuring your peace of mind. Our advanced technology instantly detects and alerts you to any suspicious activity, across all devices and third-party partners, keeping you one step ahead of cybercriminals.
Monitor Your Emails and Corporate Domains Daily With EvolveID
Stolen usernames and passwords leaked on the internet are the leading way companies are hacked. With EvolveID, you can rest assured that your passwords are being monitored around the clock for any signs of a leak. Our advanced technology scans the dark web and other underground sources for passwords and usernames that have been stolen and leaked. If we detect a potential threat, we'll immediately alert you so that you can take action to secure your accounts.
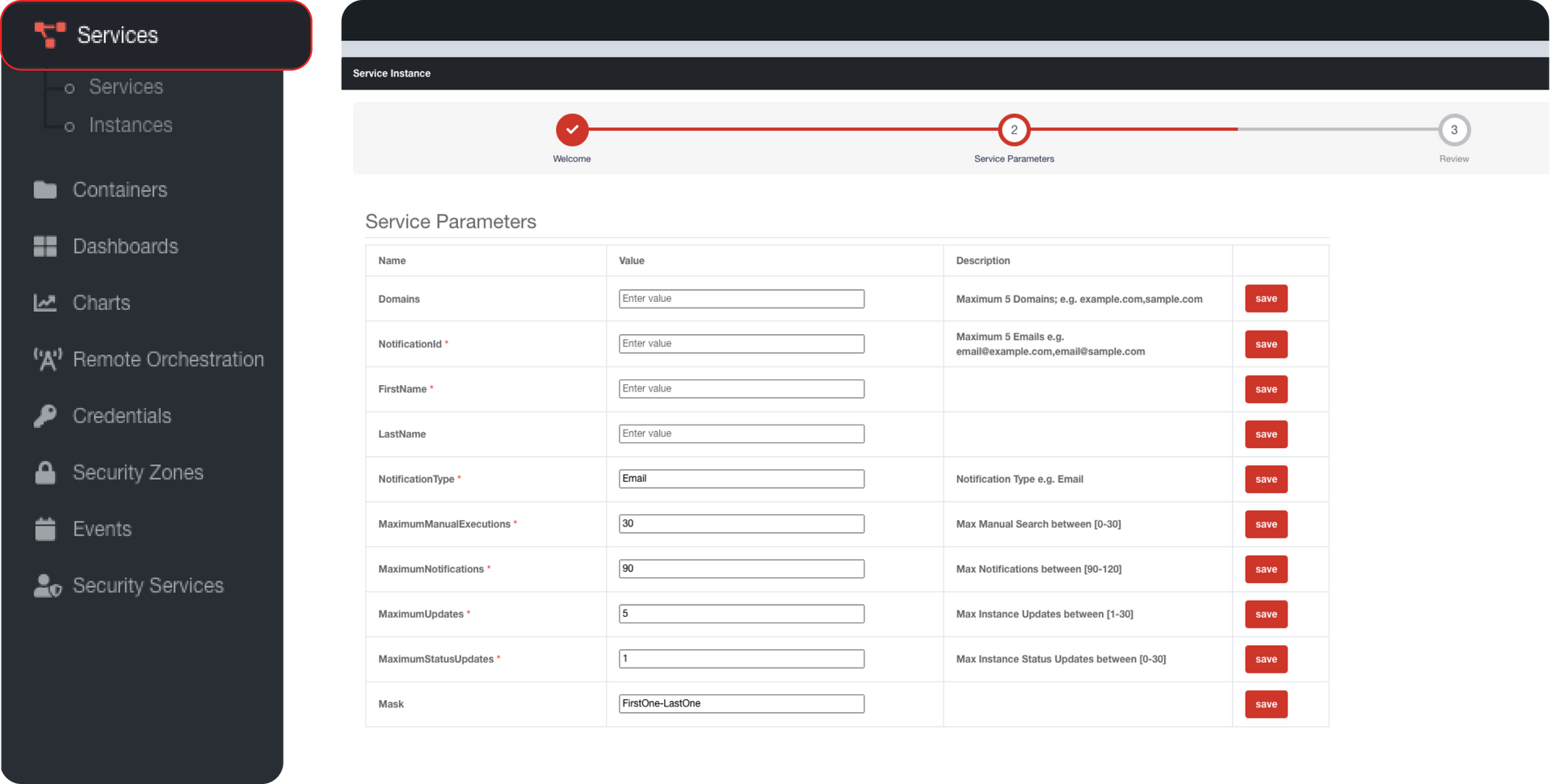
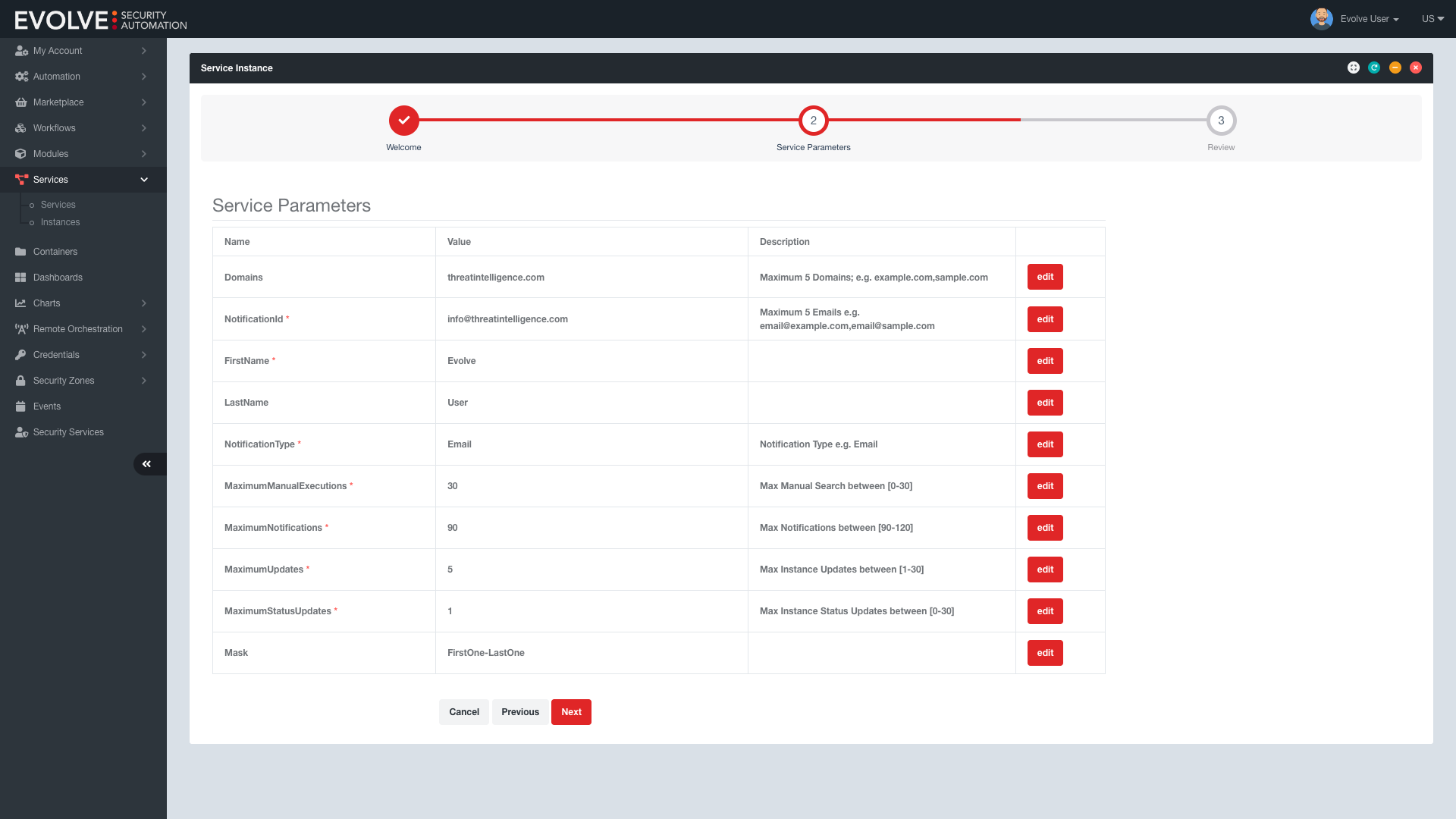
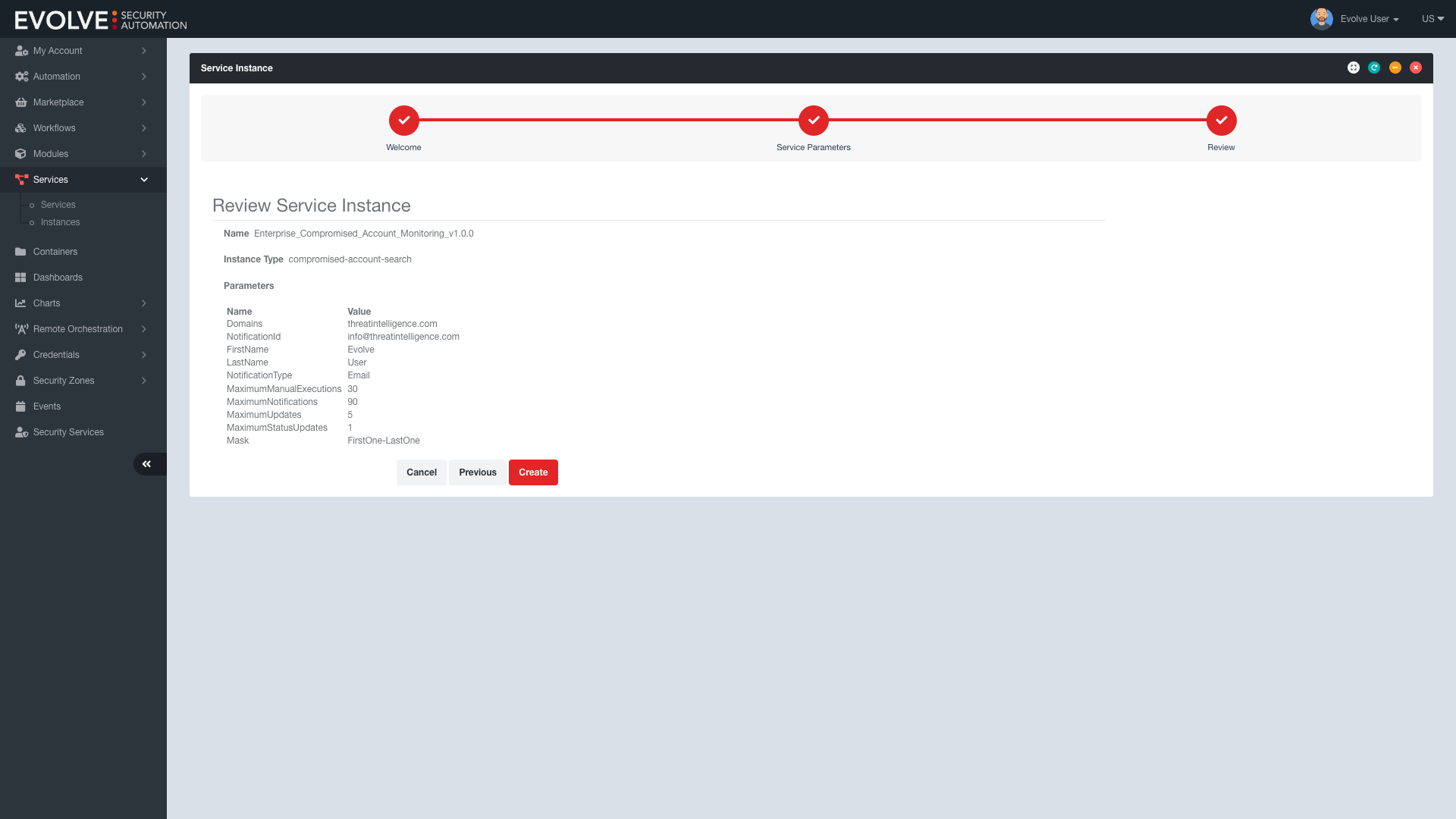
With the increasing number of passwords used in businesses, it becomes increasingly difficult to manage and monitor them effectively. An automated leaked password monitoring service like EvolveID solves this by monitoring employee passwords and alerting you when any of them appear on leaked password databases, so that you can change your passwords immediately and reduce the risk of a data breach. EvolveID lets you monitor up to 5 company domains with up to 3,000 results for each notification.
Password Management and Monitoring
The Ultimate Defense Against Stolen Credentials
EvolveID offers additional options that can further protect your business from the next data breach. Configure password masking to your preferences and monitor multiple corporate domains for added security. Get a breach summary and timeframes for complete visibility and control over your security - without any human intervention and completely on-demand. Plus, with cost optimization settings, you can enjoy all these benefits within your budget.
The New Standard in Compromised Account Monitoring
Unrivalled by any other service, EvolveID searches over 700 billion compromised accounts from thousands of security breaches that have occurred over the past decade – 100 times larger than the most commonly known service on the internet. Get the most comprehensive compromised account list available on the market with EvolveID.

Proactive Protection
Constantly monitor your corporate accounts and domains for signs of compromised credentials.

Reduce Breach Risk
Protect yourself from identity theft, account takeovers, and the consequences of a data breach with real-time monitoring of your email accounts and domains and notifications when your accounts are compromised.

Integrated Monitoring
EvolveID helps you to integrate compromised accounts with your internal systems for fast and effective risk reduction.
Key Features
- 700 Billion Compromised Accounts
- 100 Times the Coverage Evolve API Integration
- On-Demand Compromised Account Search
- Multiple Email Account Monitoring
- Real-Time Email Notifications
- Cost Optimization Settings
- Password Masking Configurations
- Multiple Corporate Domain Monitoring
- Breach Summary and Timeframes
Selected to conduct and manage penetration testing examinations for the Australian Government, our team members not only hold positions on the Board of Directors of CREST Australia and New Zealand, but also lead the CREST Technical Team.

With extensive experience in the longest running training course at Black Hat USA and a position on the Black Hat Asia Review Board, our trainers are renowned for their expertise in the most recent threats and the cutting-edge techniques to combat them.

Threat Intelligence contributes to the development of global security methodologies, standards, and libraries that are incorporated into industry-specific security regulations of the Open Web Application Security Project (OWASP).

The Team Behind Evolve
Ready to Get Started?
Is your organization looking for a complete cyber security solution? With our products and services, your team can take a propositive security posture. Let’s chat.